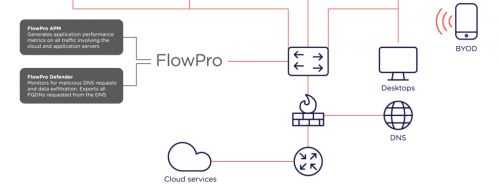
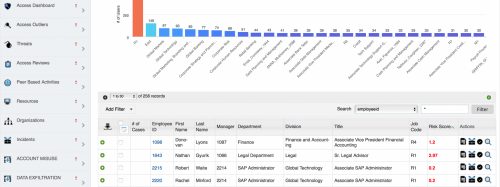
Like any defence, lines weaken as they extend – or, at least, this is true without sufficient preparation and the pre-emptive strategies. For networks, this means effective tools for monitoring and gating edge traffic with inline security solutions.
Tell us what you want to achieve and we’ll get in touch…