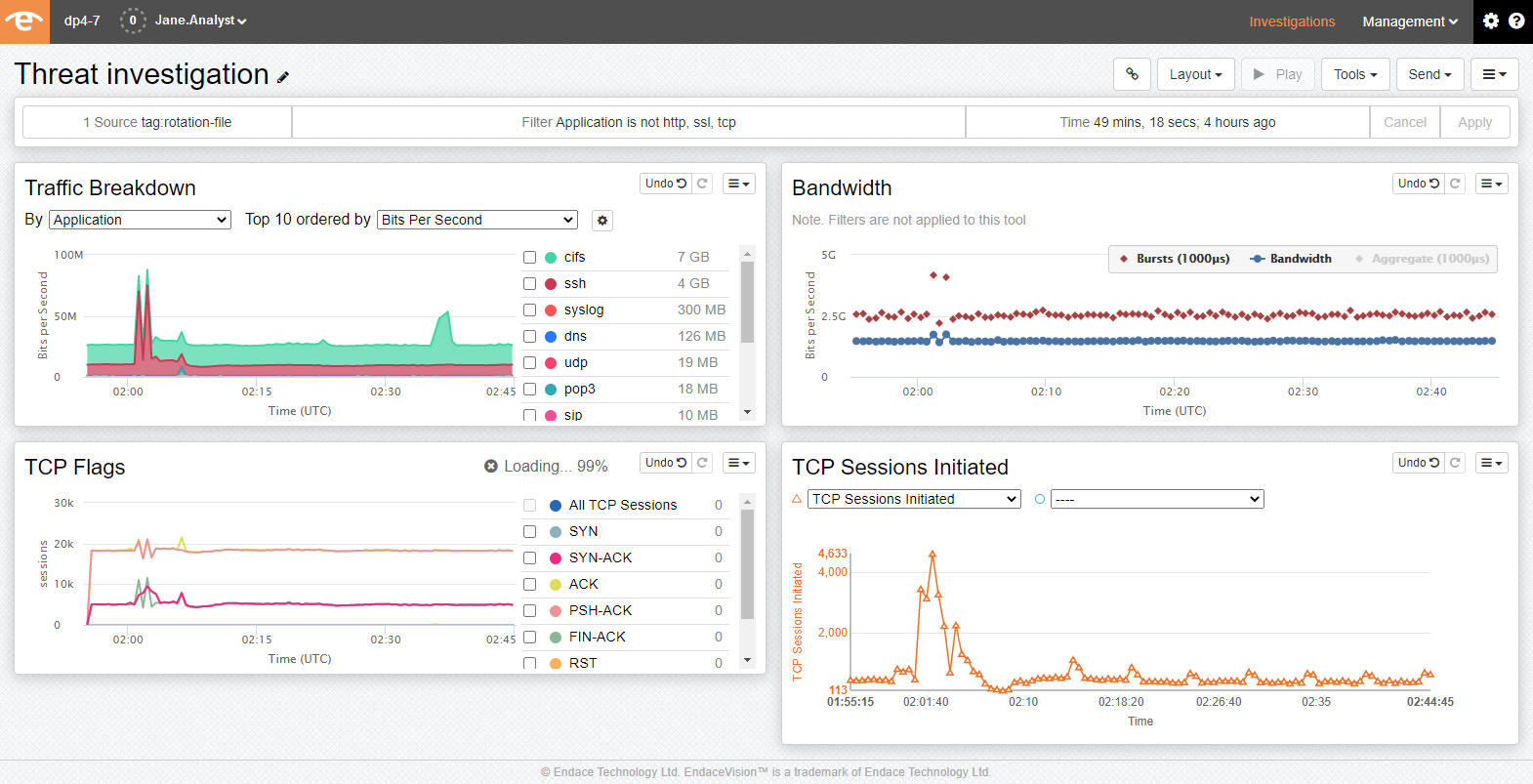
The challenge of cybersecurity has always been in its unpredictability. Technology is continually evolving. New applications and capabilities deliver potential new vulnerabilities, which are readily exploited by would-be infiltrators. Network security is an attempt to keep apace: to evolve the tools and solutions used to prevent or mitigate cyberattacks through, more than anything, the monitoring and gathering of relevant and accurate data.
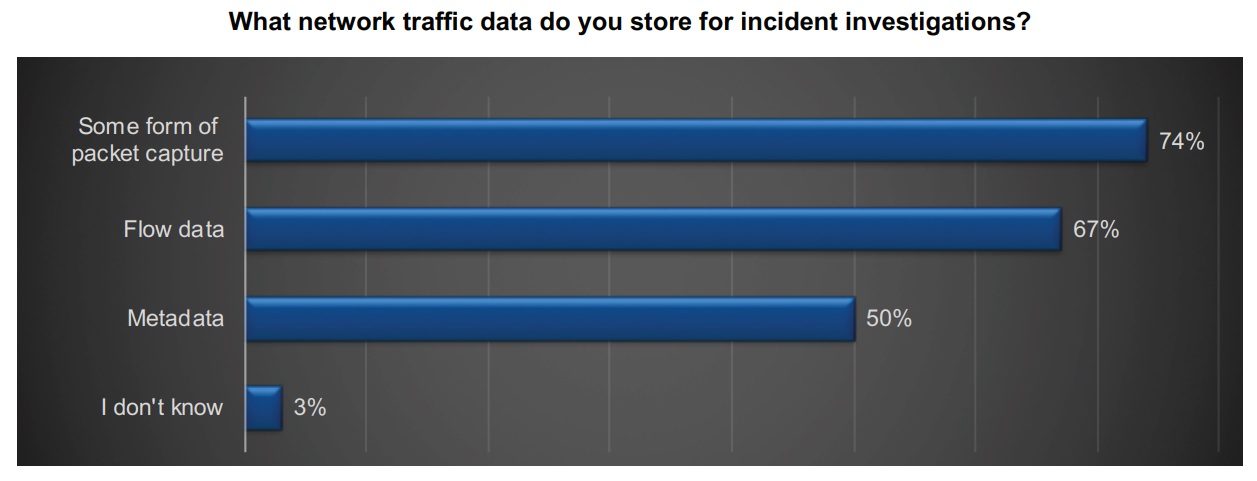
This is why more and more organisations are prioritising packet capture in their incident identification and resolution process. A report by Endace has found that, whilst network managers identified data as the best means to detect security breaches, packet capture is a primary source of that data. Of the study’s respondents, 67% of organisations reported using flow data, whilst 74% reported collecting information from packet capture as a primary means of incident investigation.
Why historical data wins against real-time data
Real-time data monitoring is critical for maintaining network performance and security, but its capacity to help detect early breaches is limited. That’s because real-time data provides a picture without the narrative; the lessons have not yet been learnt, the patterns have not been given an opportunity to form and the data, whilst useful, is unable to immediately make clear the resolution pathway.
This is why a change of strategy is required. Endace’s research identified that 78% of organisations aren’t comfortable with their current cyber risk; it also identified, perhaps unsurprisingly, that senior management was more positive and confident than the frontline operations personnel. Additionally, only 28% of organisations reported feeling effective at proactively identifying security gaps, and only 47% believe they have the tools required to attempt to achieve this.
Maintaining monitoring whilst mitigating risk
More cybersecurity software doesn’t necessarily mean better security – or greater confidence. An assembly of software can distort perception or even introduce additional risk. Different programs have different strengths and weaknesses, and rarely speak to one another on the level required to produce effective insight that can inform in-the-moment incident resolution.
The key is in having the correct assembly of software. Or, more accurately, the correct assembly of capabilities. Key to the report’s findings was that organisations using packet capture expressed greater confidence in their cybersecurity readiness. The readiness of packet capture is, indeed, more literal; it means having access to key information both in the moment and over time, to know the behaviours, analyse trends, and be able to identify threats in their infancy. But to achieve this, packet capture must always be there: a permanent part of the network security manager’s toolset that is relied upon daily, rather than utilised only on-demand. The report shows that those that had this were able to respond faster – with greater detection accuracy – had identified workflows for effective resolution, and boasted significantly improved network visibility.
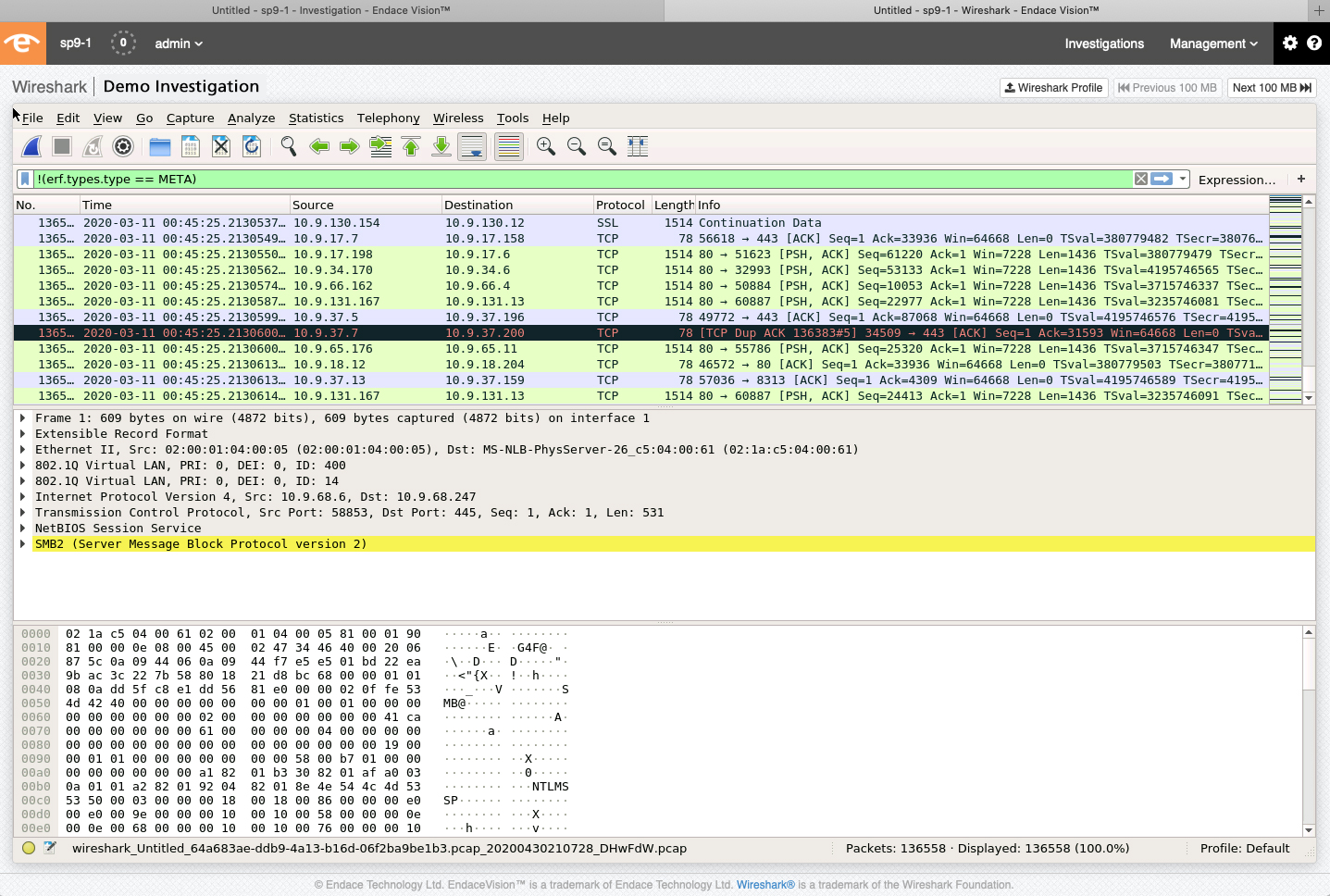
Network packet capture does not tell the whole story, but it tells everything needed to act: up to 99% of daily activities across a network. Those with it feel more confident and are better prepared. They’re able to detect and resolve issues faster, and better protect their business from cybersecurity threats. Retaining this information also has the aggregate benefit that the more traffic that is captured, the more resilient the network becomes. The result is an understanding of the idiosyncrasies of traffic, the contexts in which it arises, and an awareness of both the minor and major alarm bells of cybersecurity threats.
The EndaceProbe Analytics Platform holistically improves network security by monitoring and capturing accurate, quality data, enabling you to see more, respond better, and feel confident about your network’s security. To learn more about packet capture or EndaceProbe, contact us today.