Offence and Defence
The world’s major nations are scaling up their cyber offensive capabilities with a surprisingly broad range of governments and businesses being targeted. This article in The Guardian even goes as far as describing an active ”cyberwar” between west and east. Network infrastructure such as routers, switches and firewalls are being exploited everywhere, in many cases for “man in the middle” attacks on devices at 3rd party organisations, to provide ongoing access for intellectual property theft and future offensives.
Much of the hacking and malware activity that cyber warfare consists of is carried out on the target network very discreetly, and in most cases will go unnoticed. For this reason, it is important to use a method know as “baselining” to determine what normal activity looks like on your network. Next, you’ll need to run algorithmic behavioural analysis on your traffic, preferably at every device, to detect any suspicious behaviour and alert on it.
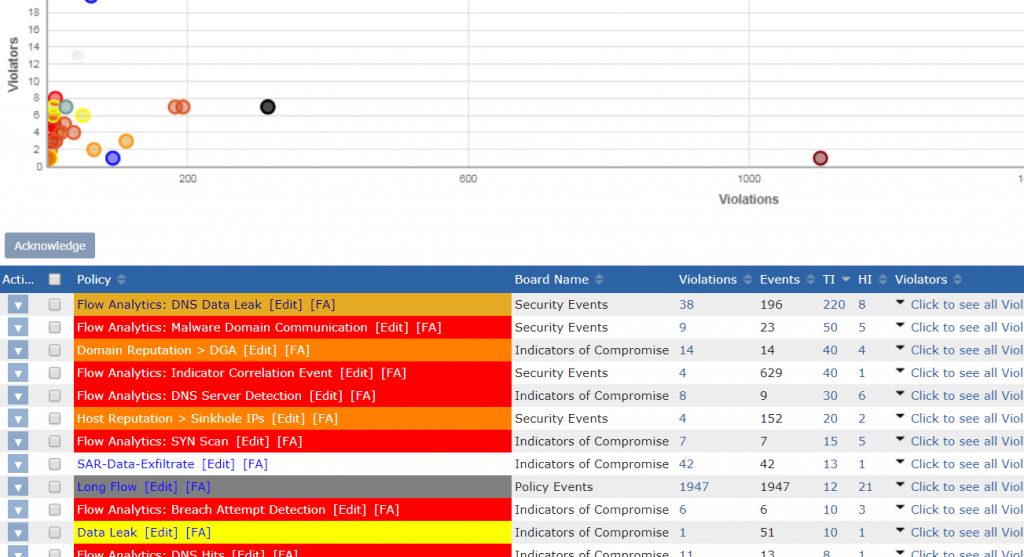
The indicator of compromise correlation engine in Plixer’s Scrutinizer is designed to help prioritise potential security issues for further investigation.
We recommend Scrutinizer by Plixer for network traffic analysis. Intensively developed and updated it has lead the market for network metadata collection and analysis since 1999.
Next Steps…


